DIVD-2021-00027 - Apache HTTP 2.4.49 Path Traversal and File Disclosure
| Our reference | DIVD-2021-00027 |
| Case lead | Ralph Horn |
| Author | Diego Klinkhamer |
| Researcher(s) |
|
| CVE(s) | |
| Product | Apache HTTP Server |
| Versions | 2.4.49/2.4.50 |
| Recommendation | Upgrade to 2.4.51 |
| Patch status | Full patched |
| Status | Closed |
| Last modified | 12 Aug 2022 11:21 CEST |
Summary
Apache HTTP Server project version 2.4.49 has a vulnerability in their path normalization which allows an attacker to map URLs to files outside the document root by launching a path traversal and file disclosure. The vulnerability can also be bypassed in apache 2.4.50. As there has been evidence of exploitation in the wild we advice to patch with high priority.
What you can do
If you run Apache HTTP server version 2.4.49/2.4.50, downgrade to 2.4.48 or upgrade to 2.4.51.
What we are doing
We are actively scanning for vulnerable machines on the internet.
Timeline
| Date | Description |
|---|---|
| 29 Sep 2021 | CVE-2021-41773 reported by the ASF security team. |
| 04 Oct 2021 | CVE-2021-41773 patched and documented |
| 05 Oct 2021 | First version of this case file |
| 05 Oct 2021 | DIVD is actively scanning for vulnerable servers. |
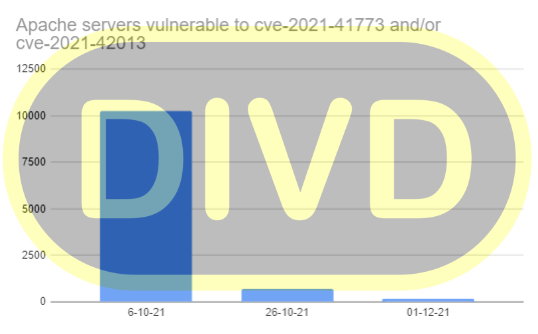
| 06 Oct 2021 | First round of notifications sent about 10269 vulnerable hosts |
| 07 Oct 2021 | Apache 2.51 released to mitigate {% cve CVE-2021-41773 %} |
| 26 Oct 2021 | Rescanned the internet. Second round of notifications sent about 6945 vulnerable hosts |
| 01 Dec 2021 | Based on final scan, 158 vulnerable hosts have been identified. Notifcations sent |
| 01 Dec 2021 | Case closed |
gantt
title DIVD-2021-00027 - Apache HTTP 2.4.49 Path Traversal and File Disclosure
dateFormat YYYY-MM-DD
axisFormat %e %b %Y
section Case
DIVD-2021-00027 - Apache HTTP 2.4.49 Path Traversal and File Disclosure (57 days) :2021-10-05, 2021-12-01
section Events
CVE-2021-41773 reported by the ASF security team. : milestone, 2021-09-29, 0d
CVE-2021-41773 patched and documented : milestone, 2021-10-04, 0d
First version of this case file : milestone, 2021-10-05, 0d
DIVD is actively scanning for vulnerable servers. : milestone, 2021-10-05, 0d
First round of notifications sent about 10269 vulnerable hosts : milestone, 2021-10-06, 0d
Apache 2.51 released to mitigate {% cve CVE-2021-41773 %} : milestone, 2021-10-07, 0d
Rescanned the internet. Second round of notifications sent about 6945 vulnerable hosts : milestone, 2021-10-26, 0d
Based on final scan, 158 vulnerable hosts have been identified. Notifcations sent : milestone, 2021-12-01, 0d
Case closed : milestone, 2021-12-01, 0d
More information
- Path Traversal Zero-Day in Apache HTTP Server Exploited
- Apache fixes actively exploited web server zero-day
- NCSC Advisory NCSC-2021-0861