DIVD-2022-00009 - SolarMan backend administrator account/password
| Our reference | DIVD-2022-00009 |
| Case lead | Frank Breedijk |
| Researcher(s) |
|
| CVE(s) |
|
| Products |
|
| Versions |
|
| Recommendation | Consider the risks when using these products |
| Patch status | n/a |
| Workaround | n/a |
| Status | Closed |
| Last modified | 09 Aug 2024 09:59 CEST |
Summary
Triggered by a tweet from Célistine Oosting, Jelle Ursem decides to look for SolarMan credits and finds a (now removed) GitHub repository containing a username and password.
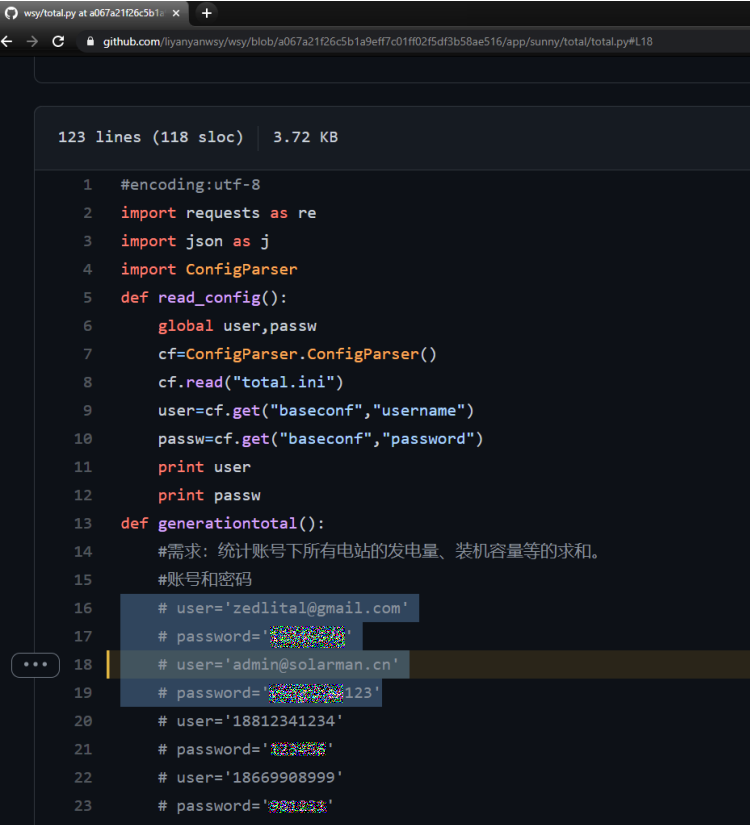
Turns out this is indeed the Super Admin account and working password. Since the account doesn’t have MFA Jelle was able to log in with the username and password.
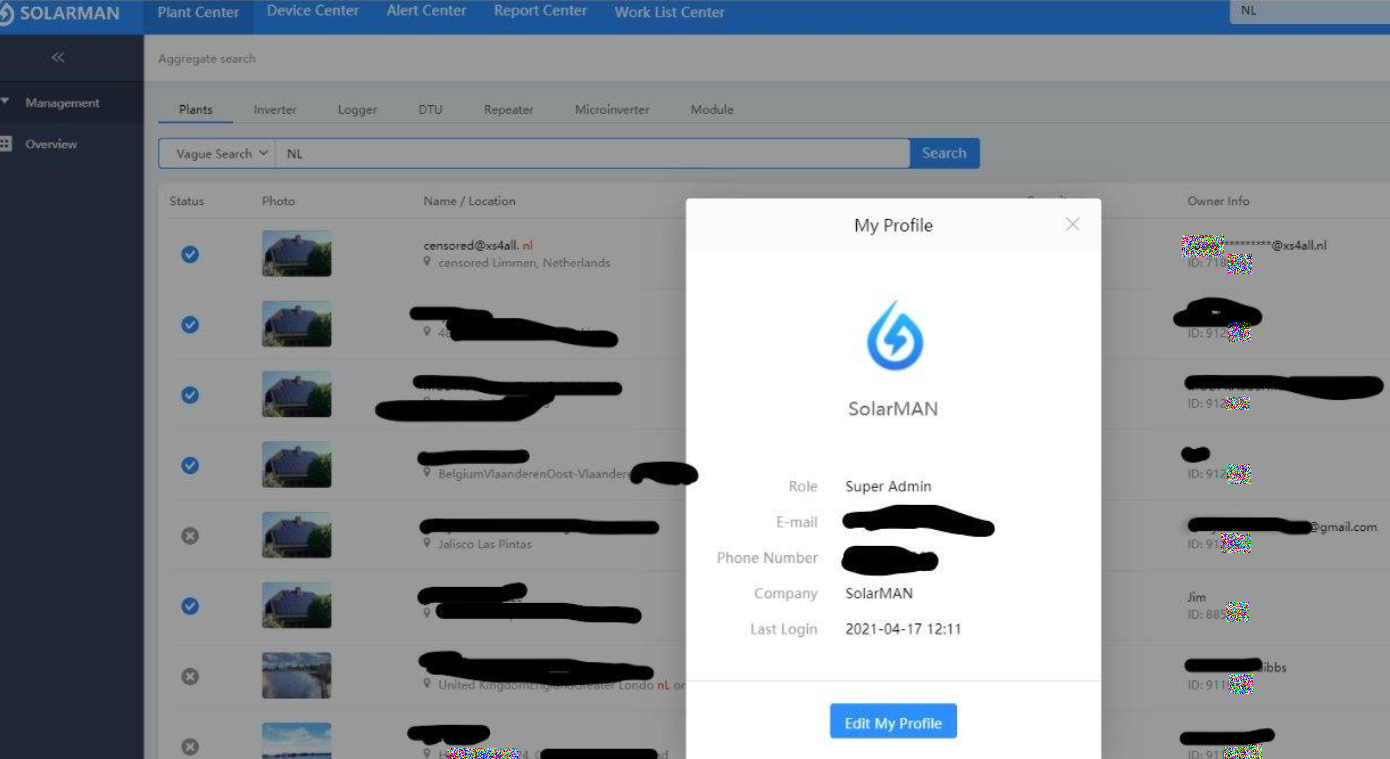
This backend and the Super Administrator account give the ability to:
- See all data from all customers including:
- GPS coordinates
- Current and historical production data
- Current faults
- Clearing of faults
- Downloading firmware
- Uploading of firmware to devices
- Creation and deletion of customers
In the SolarMan platform, there are almost 1,000,000 plants (installations) with a total power of over 10GwP (actually generated). Most systems are located in China and Australia, but a significant number of 40k+ in The Netherlands.
In the second half of April 2021, SolarMan gets notified and changes the password. On 3 Feb 2022, Jelle reads Jan van Kampen’s blogpost on Growatt and decides to check the password again. To his horror, the password has been changed back to the password in the GitHub repo.
On 4 Feb Jelle joins DIVD and on 6 Feb we opened this case.
Getting the account closed turned out to be hard. The first time the vendor responded promptly, but silently. In fact, neither we nor the NCSC-NL ever got any reply from them. NCSC-NL used the help of the Dutch Embassy in China and head of research Victor Gevers visited the Chinese Embassy in The Hague, all in an effort to get into contact. In the end, the password has been changed and the repository deleted. Just before this Cert China confirmed receipt of the report to NCSC-NL.
The net effect of deleting the repository and resetting the password is that the number of parties with the ability to abuse this access has been reduced from “everybody that was able to find the password on GitHub” to the vendor and whoever can control the vendor.
On 24 Jul 2022 we presented out findings at the MCH2022 hackers camp. You can watch the presentation online or below.
The vendor responded to our disclosure right before we got on stage:
Dear Frank,
This is Wei and I am responsible for marketing department, thanks for your reply and thanks anyway for
Dutch ethical hacker finding a issue for us.
At present we're absolutely off the court with the upcoming disclosure and communicating time left to
us is extremely limited.
For now, I can only say:
Firstly, the account is subjected to testing group and NOT a super Admin account, which later we can
provide proof in details;
Secondly, uploading firmware via the account is fine but no actual control function is workable as real
operation needs a further verification and subjected to authorization from inverter manufacutrers;
Thirdly, the account is not related to any account of other customers and won't affect their PV plants;
At last, the account is now in safe condition.
Therefore, we believe there is no effect to PV plant operating in the system.
In case you wanna go to public with the case, please do keep above facts in your statement.
And we expect not to mention the product name in disclosure and don't expect any exaggration before
clarification..
Personally I think we can create a long term cooperation with your organization to offer serivce to our
customer in much more secure way
On 9 Aug 2022 we asked the vendor to clarify these statements :
Wei,
I have some questions with regards to you email below.
With regards to the Super User account. We did confirm we were seeing live data from actual users in the
dashboard, not test data. We actually visisted one of your custoemrs and all the details including the GPS
coordinates turned out to be real.
When you say: "the account is subjected to testing group and NOT a super Admin account" what do you mean by
that and what proof can you provide?
We also noticed that the account was not protected with dual factor authetication (2FA) or multi factor
authentication (MFA), why not?
When you say: "uploading firmware via the account is fine but no actual control function is workable as
real operation needs a further verification and subjected to authorization from inverter manufacutrers" what
do you mean by this?
You say: "Thirdly, the account is not related to any account of other customers and won't affect their PV
plants" what does this mean? We were able to see a large list of Solarman, Omnik and other inverter customers.
When you say: "At last, the account is now in safe condition." does this mean the accoutn is not also
protected by MFA?
You said: Personally I think we can create a long term cooperation with your organization to offer serivce to
our customer in much more secure way
I hope we can establish that relation indeed. Our goal always to make the internet more safe by reporting
findings to the people that can actually address those findings.
Frank
We have since asked both Wei personally as well as Solarman via LinkedIn to respond to our email. On 9 Sep 2022 we were still to receive a reply.
What you can do
Not much. End users do not have any control over these events.
However, when installing smart devices please consider that:
- Your data is often uploaded to the vendor
- The vendor may change
- The vendor has ultimate control over the device
- When the vendor gets compromised, your device can be compromised as well
What we are doing
This case has been closed. We are not taking any further action.
We have presented the details of this case at the MCH 2022, hack camp on Sunday 24 July at 12:40, a video recording is avilable.
Based on the questions by Dutch representatives Queeny Rajkowski and Silvio Erkens the Dutch Telecom Autority will start an investigtion into the security of PV inverters.
Timeline
| Date | Description |
|---|---|
| 05 Aug 2019 | Password(s) committed to GitHub repository |
|
05 Aug 2019- 24 Apr 2021 |
Password exposed and service vulnerable - 1st time |
| 16 Apr 2021 | Célistine Oosting, tweets that Omnik converter is now uploading data to China |
| 17 Apr 2021 | Jelle finds working password for SolarMan Super Admin account in Github repo |
| 17 Apr 2021 | Vendor informed |
| 24 Apr 2021 | Password changed |
| 03 Feb 2022 | Jelle discovers that password was changed back to password in GitHub repo |
|
03 Feb 2022- 02 Jul 2022 |
Password exposed and service vulnerable - 2nd time |
| 06 Feb 2022 | Case opened |
| 06 Feb 2022 | Vendor notified |
| 07 Feb 2022 | DIVD involves the Dutch National Cyber Security Center (NCSC) |
| 20 Feb 2022 | NCSC notifies vendor and Cert-CN |
| 15 Apr 2022 | NCSC notifies Cert.cn |
| 10 May 2022 | NCSC involves the Dutch embassy in China. |
| 09 Jun 2022 | NCSC and China Cert in contact. The case file has been given to China Cert |
| 17 Jun 2022 | DIVD contacts our office neighbor, the Chinese consulate in The Hague. We are given an (unnamed) liaison at China Cert |
| 26 Jun 2022 | Dutch representatives Queeny Rajkowski, Silvio Erkens have asked questions to minister Yesilgöz-Zegeriu and minister Jetten based on the publication in Follow the Money |
| 02 Jul 2022 | Account is closed and GitHub repo removed |
| 02 Jul 2022 | Case closed |
| 03 Jul 2022 | NCSC reports that the Dutch ambassador has sent a formal letter to China Cert who confirmed receipt of the data |
| 24 Jul 2022 | Findings presented at MCH2022 |
| 24 Jul 2022 | Vendor responded |
| 09 Aug 2022 | DIVD asks the vendor to clarify the statments they mode based on our case. |
|
09 Aug 2022- 09 Sep 2022 |
Waiting for vendor to respond |
| 02 Sep 2022 | Dutch ministers Yesilgöz-Zegeriu and Jetten answer the questions asked by representatives Queeny Rajkowski and Silvio Erkens |
| 09 Sep 2022 | To date DIVD has not received a response from Solarman |
More information
- Tweet that triggered the investigation by Célistine Oosting
- Tweet in which Jelle makes his find public for the first time
- Now deleted GitHub repository
- Jan van Kampen’s blogpost on Growatt
- News article about Dutch government blocking a Chinese party from the Dutch grid
- Video recording of presentation at Hackers Camp MCH 2022
- Official questsion of dutch representatives Queeny Rajkowski and Silvio Erkens to ministers Yesilgöz-Zegeriu and Jetten
- Official answers of ministers Yesilgöz-Zegeriu and Jetten to the questsion of dutch representatives Queeny Rajkowski and Silvio Erkens