DIVD-2020-00001 - Citrix ADC
| Our reference | DIVD-2020-00001 |
| Case lead | Frank Breedijk |
| Researcher(s) |
|
| CVE(s) | |
| Product | Citrix ADC / Citrix Gateway / Netscaler ADC / Netscaler Gateway / Citrix SD-WAN WANOP |
| Versions | ADC versions 10, 11.1, 12.0, 12.1 and 13 <br> SD-WAN WANOP versions 10.2.6 and 11.0.3 |
| Recommendation | Don't use unpatched systems. Make sure systems are not compromised/backdoored before patching |
| Patch status | Available |
| Workaround | Available but not 100% effective |
| Status | Closed |
| Last modified | 12 Aug 2022 11:21 |
Update 9-3-2020 21:12
Gezien de lage hoeveelheid ip adressen die nog kwetsbaar zijn gaan we deze case afsluiten.
Samenvatting
Op 24-12-2019 werd bekend dat het product Citrix ADC / Citrix Gateway / Netscaler ADC / Netscaler Gateway (hierna Citrix ADC) een ernstig lek bevat waardoor het eenvoudig mogelijk is het systeem over te nemen. Voor versie 11.1 en 12.0 zijn inmiddels patches beschikbaar. Voor de andere versies worden de patches op 24-1 verwacht. Voor het downloaden van patches is een Citrix portal account nodig. Voor systemen waar nog geen patches voor zijn/waren is er een mitigatie beschikbaar die de kwetsbaarheid verminderd. Deze bleek echter niet 100% betrouwbaar. Het NCSC adviseert dan ook indien mogelijk Citrix ADC systemen zonder patch niet te gebruiken.
Aanvallers scannen massaal het internet af naar kwetsbare systemen die vervolgens worden overgenomen.
Op basis van een risico analyse is het verstandig, alvorens de patches te installeren, uit te sluiten of het systeem reeds door aanvallers is gecompromitteerd.
- Indien de mitigerende maatregel voor 9-1-2020 is toegepast en er geen gebruik gemaakt werd van versie 12.1 build 50.28 dan is de kans klein dat het systeem reeds gecompromitteerd is.
- Indien de mitigerende maatregel na of op 9-1-202 is geïmplementeerd of als er gebruik gemaakt is van versie 12.1 build 50.28 dan is het verstandig extra maatregelen te nemen.
- Zorg er in ieder geval voor dat u de patch uit betrouwbare bron ontvangt. Liefst van de Citrix site zelf.
Additionele maatregelen zijn:
- Koppel het systeem af.
- Laat het systeem door een deskundige forensisch onderzoeken (zie onze blog), zorg dat dit onderzoek wordt uitgevoerd door een voldoende kundige expert.
- Controleer het systeem op bekende IOC’s (Indicators Of Compromise).
- Laat verder forensisch onderzoek uitvoeren als er aanwijzignen zijn dat het systeem inderdaad gecompromitterd is.
- Als het systeem gecompromitteerd is, dan zijn ook de sleutels van de TLS certificaten gecompromitteerd. Laat deze certificaten intrekken door de uitgevende partij een vraag nieuwe exemplaren aan op basis van nieuwe sleutels. Indien gebruik is gemaakt van “wildcard” certificaten, dan moeten deze vervangen worden op alle systemen waarop zij gedeeld worden.
- Bouw een nieuw schoon systeem op en voorzie dit nieuwe systeem wederom van de mitigatie.
- Voer een riciso analyse uit wat deze inbraak verder voor u/uw organisatie betekent.
(Met dank aan NCSC Advies)
Het Security Meldpount scant naar systemen waarvan wij op afstand vast kunnen stellen dat de mitigatie niet is uitgevoerd of werkt en sturen hiervan bericht naar de beheerders van het netwerk waar deze systemen in staan. Hierbij concentreren wij ons op systemen in of gelieerd aan Nederland.
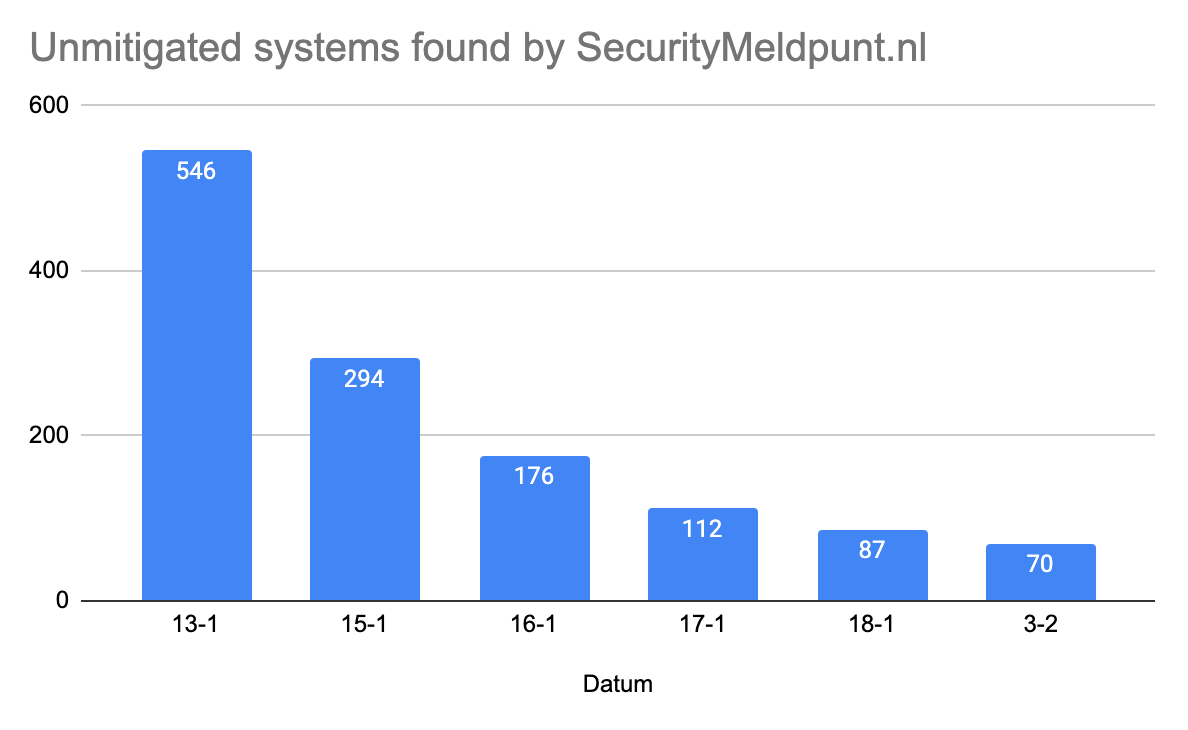
Het aantal ongemitigeerde systemen neem gelukkig af.
Tijdslijn
| Datum | Omschrijving |
|---|---|
| 17-12-2019 | Citrix meldt een kwetsbaarheid in Citrix ADC. En raadt iedereen aan om op deze systemen een mitigatie te implementeren. |
| 9-1-2019 | Onderzoekers melden dat er actief gezocht wordt naar kwetsbare systemen. |
| 11-1-2020 | Exploit code is publiek beschikbaar o.a. van Project Zero Day India en Trusted Sec. |
| 13-1-2020 | Het Nederlands Security Meldpunt activeert zichzelf. |
| 14-1-2020 | Eerste notificaties worden uitgestuurd door Het Security Meldpunt. |
| 15-1-2020 | Blog post met links naar artikelen om vast te stellen of een ADC gecompromitteerd is. |
| 16-1-2020 | Het NCSC meldt dat de mitigatie niet betrouwbaar is en adviseert te overwegen Citrix ADC systemen af te sluiten. Het Security Meldpunt besluit het scannen en melden tijdelijk te staken. |
| 17-1-2020 | Het NCSC verduidelijkt het advies van 16-1: “Schakel Citrix-systemen uit waar dat kan of tref aanvullende maatregelen”. het Security Meldpunt gaat door met scannen en melden. |
| 19-1-2020 | Patches beschikbaar voor versie 11.1 and 12.0. Dit is één dag eerder dan eerder gecommuniceerd. De datum waarop patches voor versie 12.1 en 13 is vervroegd van 27-1 naar 24-1. De datum waarop parches voor versie 10 beschikbaar zijn is vervroegd van 31-1 naar 24-1 |
| 24-1-2020 | Citrix verwacht op deze datum patches beschikbaar te hebben voor versie 10, 12.1 en 13 van Citrix ADC en voor SD-WAN WANOP. |
| 26-1-2020 | Citrix heeft de definitieve patches (eerder) uitgebracht voor alle versies. Daarnaast is er een testtool beschikbaar gesteld om te controleren of er potentieel misbruik is gemaakt van de kwetsbaarheid en er IOC’s op het systeem aanwezig zijn. |
| 9-3-2020 | Case Closed |
English
Update 9-3-2020 21:12
Considering the low amount of vulnerable ip addresses coming from our scans, we deciced to close this case.
Summary
On 24-12-2019 Citrix ADC / Citrix Gateway / Netscaler ADC / Netscaler Gateway (hereafter Citrix ADC) appeared to contain a serious vulnerability that allows an attacker to trivially take over a system. Patches are available for version 11.1 and 12.0. Patches for the other versions are expected on 24-1. A valid Citrix portal account is needed to download these patches. For systems that are currently upatched there is a mitigation that reduces the vulnerability. However, this mitigation turned out not to be 100% reliable. The Dutch NCSC strongly recommends to not use Citrix ADC systems that are unpatched if possible (translation by google.
Attackers are bulk scanning the internet for vulnerable systems and exploiting them.
Use the following risk analysis to determine your cause of action before patching:
- If the mitigation was implemeneted before 9-1-2020 and version 12.1 build 50.28 was used not used the changes that the system is compromised are slim, you can install the patches on your system
- If the mitigation was implemented on or after 9-1-2020 or version 12.1 build 50.28 was used, it is recommended to take additional measures.
- Make sure you patch or image comes from a realiable source , preferably the Citrix website.
Additional measures are:
- Disconnect the system
- Make sure an expert forensically investigates the sytem (see our blog), make sure that the expert is sufficiently qualified.
- Test your system on possible IOC’s (Indicators Of Compromise
- Perform further forensics if the system turns out to be compromised.
- If the system is compromised, then the keys TLS certificates on the system must be considered to be compromised as well. Ask your CA to revoke these certificates and request new certificates based on new keys. If the system contained “wildcard” certificates, then make sure these are replaced on any other systems that use them as well.
- Build a new clean system and re-apply the mitigation.
- Perform a risk analysis to determine the consequences of this hack for you/your organisation.
(Met dank aan NCSC Advies)
The Security Hotline is scanning for systems that are unmitigated or have an ineffective mitigation and is sending out notifications to the operators of networks in which these systems are found. We focus on systems located or related to The Netherlands.
The number of vulnerable systems is decreasing

Timeline
Timeline
| Date | Description |
|---|---|
| 17 Dec 2019 | Citrix reports a vulnerability in Citrix ADC and advices to [implement mitigation](https://support.citrix.com/article/CTX267679 |
| 09 Jan 2019 | Researchers report attackers are actively searching for vulnerable systems. |
| 11 Jan 2020 | Exploit code is publicly available, e.g. the Project Zero Day India and Trusted Sec |
| 13 Jan 2020 | The Dutch Security Hotline has been activated |
| 14 Jan 2020 | First notifications have been sent out by the The Dutch Security Hotline |
| 15 Jan 2020 | Blog post with links to articles on how to establish whether a ADC is compromised |
| 16 Jan 2020 | The Dutch National Cyber Security Center, NCSC, reports mitigation measures prove unreliable and advices to consider to shut down Citrix ADC systems. The Dutch Security Hotline decides to temporarily stop scanning and reporting. |
| 17 Jan 2020 |
The NCSC clarifies its 16-1 statement: “Shut down Citrix systems if possible or take additional measures”. The Dutch Security Hotline continues its scanning and reporting activities. |
| 19 Jan 2020 | Patches avaiable for version 11.1 and 12.0. This is one day sooner then initially communicated. The date for which patches for version 12.1 and 13 are available has changed from 27-1 to 24-1. The date that patches are available for version 10 has been changed from 31-1 to 24-1. |
| 24 Jan 2020 | Citrix expect to have patches available for version 10, 12.1 and 13 of ADC and SD-WAN WANOP |
| 24 Jan 2020 | Citrix deploys the final patches for all versions. Also an Indicator of Compromise Scanning tool has been released to test possible exploitation |
| 09 Mar 2020 | Case Closed |